This is a PowerShell script that will find the name of a system that is locking out an end user’s AD account. First you have to enable auditing of event logs on your Domain Controller (DC). This will help to gleam more information about the system causing the lockout.
Step 1. Enabling Auditing
The event ID 4740 needs to be enabled so it gets locked anytime a user is locked out. This event ID will contain the source computer of the lockout.
1. Open the Group Policy Management console. This can be from the domain controller or any computer that has the RSAT tools installed.

2. Modify the Default Domain Controllers Policy
Browse to the Default Domain Controllers Policy, right click, and select edit.
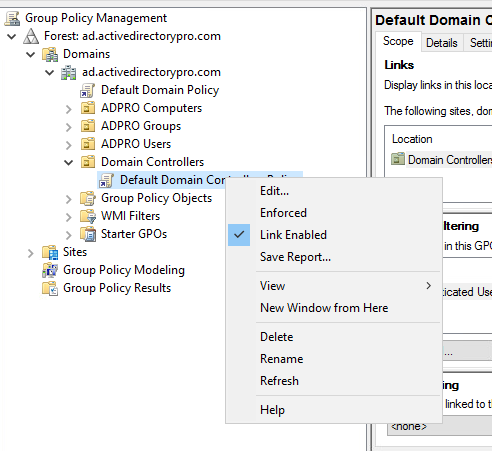
3. Modify the Advanced Audit Policy Configuration
Browse to computer configuration -> Security Settings -> Advanced Audit Policy Configuration -> Audit Policies -> Account Management
Enable success and failure for the “Audit User Account Management” policy.
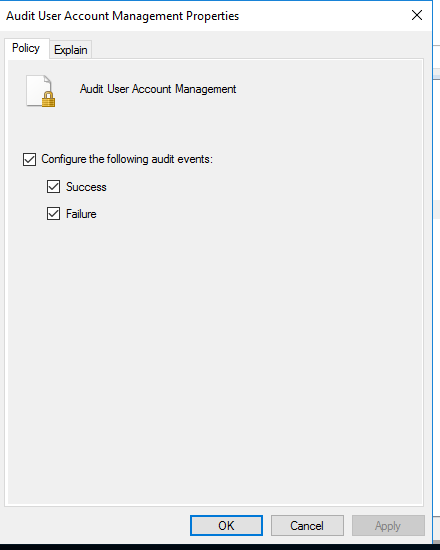
Auditing is now turned on and event 4740 will be logged in the security events logs when an account is locked out.
Step 2. Running the Script
The script will query for the Primary DC and then search for event 4740. When finished it will create a file ” Get-ADUserLockouts_List_ TimeStampHere” This way you will always have a unique file name without writing over the original.
$Today = Get-Date
Import-Module ActiveDirectory
#Get main DC
$PDC = (Get-ADDomainController -Filter * | Where-Object {$_.OperationMasterRoles -contains "PDCEmulator"})
#Search PDC for lockout events with ID 4740
Write-Host "Searching for account lockouts."
Write-Host "Please wait for it to finish and then check Get-ADUserLockouts_List.txt file" -ForegroundColor Green
$LockedOutEvents = Get-WinEvent -ComputerName $PDC -FilterHashtable @{LogName='Security';Id=4740} -ErrorAction Stop | Sort-Object -Property TimeCreated -Descending
#Parse and filter out lockout events
Foreach($Event in $LockedOutEvents)
{
If($Event | Where {$_.Properties[2].value -match $UserInfo.SID.Value})
{
$Event | Select-Object -Property @(
@{Label = 'User'; Expression = {$_.Properties[0].Value}}
@{Label = 'DomainController'; Expression = {$_.MachineName}}
@{Label = 'EventId'; Expression = {$_.Id}}
@{Label = 'LockoutTimeStamp'; Expression = {$_.TimeCreated}}
@{Label = 'Message'; Expression = {$_.Message -split "`r" | Select -First 1}}
@{Label = 'LockoutSource'; Expression = {$_.Properties[1].Value}}
) | Out-File Get-ADUserLockouts_List_$($Today.ToString('MM-dd-yyyy_HH.mm.ss')).txt -Append
}}Sample of text file results:
User : JDoe
DomainController : Primary-DC-01.YourDomainHere
EventId : 4740
LockoutTimeStamp : 12/28/2040 11:52:03 AM
Message : A user account was locked out.
LockoutSource : Desktop-5015-DT-11Informational:
- As this script queries the PDC for information, it will need to be ran as a Domain Admin or an account that has privilege enough to run such a script.
- The directory where you save this script will have to have permissions for you to Read, Write and Execute.
- Common causes of account lockouts can be found here.
